How often are you interrupted by robocalls?
It gets tricky to ignore them, especially when they come from legitimate-looking numbers. Some of these calls are genuine, but most are not. Scams that target unsuspecting victims are on the rise.
With Voice over Internet Protocol (VoIP), phone number authentication is a big deal — and it’s only going to get tougher.
Reputable VoIP service providers, cell phone networks, and the government have teamed up to provide a system for authenticating telephone numbers before someone’s phone rings.
Authenticating phone calls assures the identity of the originating caller. This technology is known as STIR/SHAKEN. We’ll explain how this protocol works to combat caller ID spoofing and robocalls and how it affects your business communications.
What Is STIR/SHAKEN?
STIR/SHAKEN is a combination of two acronyms:
STIR: Secure Telephone Identity Revisited
SHAKEN: Signature-based Handling of Asserted Information Using ToKENs
STIR/SHAKEN is a framework of protocols used by telephone service providers to authenticate an originating caller’s identity. STIR/SHAKEN solutions are intended to prevent malicious phone calls from being made by unauthorized parties.
Both originating service providers and terminating service providers verify caller IDs to authenticate callers and avoid fraudulent robocalls. It helps call recipients protect against caller ID spoofing and maintains their trust in the phone service.

The STIR/SHAKEN framework authenticates VoIP calls using the Session Initiation Protocol (SIP) header to transmit the authentication certificate.
For legitimate call centers, these standards aren’t hard to meet. But for illegal robocallers, STIR/SHAKEN makes it more difficult to use fake caller ID information.
Let’s take a deep dive to understand how it works.
How Does STIR/SHAKEN Work?
The telephone service provider obtains a digital certificate from a certificate authority. These digital certificates work with public key cryptography techniques and are recognized by other service providers. They help in authenticating calls.
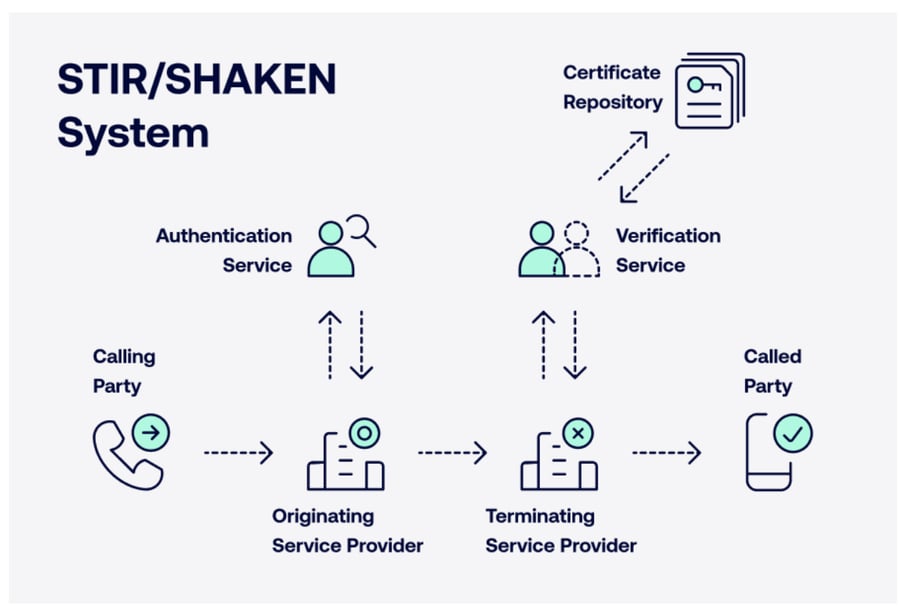
As part of the SIP protocol, STIR uses the telephone service provider’s digital signature to authenticate the caller ID. The calling party sends a SIP invite to their service provider when initiating a call. The service provider verifies the source and calling number to determine the attestation level.
There are three levels of attestation:
- Full attestation: The service provider successfully verifies the customer and their phone number. This is also called A-level attestation.
- Partial attestation: The service provider verifies the end user but not the phone number’s source. It’s also known as B-level attestation.
- Gateway attestation: The service provider can’t identify the call’s source even when it originates on a network. It’s also known as C-level attestation and is a typical case with international numbers. International call originators using the North American Numbering Plan (NANP) should give tools and information to domestic gateway providers to verify their calling identity.
Did you know? More than one-third of robocalls receive Gateway attestation levels.
Then, the service provider creates an encrypted SIP identity header and sends it to the terminating provider with the SIP invite. The information is taken up by a verification service that authenticates based on multiple factors, including the certificate’s public key, its chain of trust, and various others.
The terminating provider decides whether to allow or block a call based on attestation levels and other factors per their analytics.

Types of Scam Calls STIR/SHAKEN Can Mitigate
In essence, STIR is a technology, and SHAKEN is a policy. They work together to authenticate caller IDs and protect against multiple scams, including:
1. Phishing
Threat actors pose as genuine sources such as banks, credit card companies, or government agencies to trick victims into revealing personal information. They can try to get victims to reveal one-time passwords and other details that can compromise their identity.
STIR/SHAKEN prevents malicious attempts to spoof caller IDs, safeguarding you against phishing attempts.
2. Vishing
It’s short for “voice phishing.” Attackers trick targets into giving out sensitive information by impersonating a legitimate professional. They try to retrieve personal information or receive financial payments.
STIR/SHAKEN allows the phone company to verify if an incoming number is the same as the one on the caller ID. It prevents vishing attempts with digital validation of phone call handoff through complex networks.
3. Tech support scams
Many threat actors impersonate a company’s tech support staff to convince victims of malware in their system. They encourage targets to update the software. While updating, the victim innocently gives away remote access to their computer.
Attackers leverage this to get the victim’s personal information. Sometimes, they may install malware or ransomware on the victim’s computer. STIR/SHAKEN prevents such incidents by verifying numbers with their caller IDs.
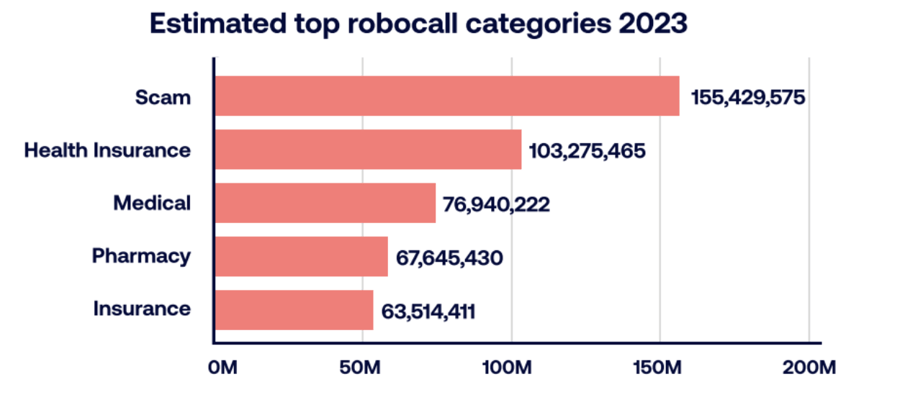
4. Robocalls
Robocalls are pre-recorded messages that may be legal or malicious. They’re genuine when the calls are about payment reminders, alerts, or incoming calls from legitimate telemarketers.
However, some of these unwanted robocalls are generated by scammers who maliciously engage victims with fake notices such as, “You have violated a traffic law, pay $X in fines to avoid full-scale legal inquiry.”
Robocalls usually promote scams or sell unwanted products. When attackers spoof the caller ID, it becomes tricky for victims to identify and block such calls. STIR/SHAKEN attests such calls and marks them spam.
Teams have more space and bandwidth to attend legitimate calls when they can easily recognize spam.
Benefits of STIR/SHAKEN
STIR/SHAKEN differentiates between genuine and spoofed calls to prevent risky telephony experiences. Here are some of its notable benefits:
- Reduces spam and robocalls: STIR/SHAKEN identifies and blocks such calls, making the business phone system more secure and reliable. The voice service provider monitors traffic patterns, identifies illegal robocalling, and helps you take appropriate actions.
- Makes caller IDs trustworthy: Subscribers are aware of legitimate calls and can prioritize them over spam, giving them more time to answer genuine callers.
- Protects against fraud: Fraud can lead to financial losses. STIR/SHAKEN helps safeguard businesses against call fraud, reducing unnecessary expenses.
- Legitimate business calls are successful: Since these call authentication standards were introduced in 2020, more service providers have signed on to allow authenticated callers through their phone networks reliably.
Why You Should Use Authenticated Numbers for Outbound Dialing
Authenticated business phone numbers help you establish the credibility of your company and deliver the initial trust needed for customers to answer calls. It offers several good things for an organization, such as:
📈 Increased call answer rates
When you register your caller ID name with the service provider and implement STIR/SHAKEN, it helps customers see that a call is genuine and comes from a legitimate source. Your calls reach customers’ ears instead of going to their voicemail.
When your caller ID is positive, customers don’t block you permanently. It prevents low attestation ratings and can lead to better sales opportunities and long-term established connections with customers.
➕ Enhanced brand reputation
You can show your commitment to customers’ security and integrity with authenticated numbers. It helps you make good first impressions as customers believe you’re a trustworthy source and not a scammer trying to impersonate you.
With your positive brand reputation, customers feel more confident answering their phones without hesitation. Conversely, if your caller ID is inaccurate, consumers may feel you are taking part in shady practices, eroding their trust in your brand.
✅ Compliance with regulations
Many countries and regulatory bodies are mandating STIR/SHAKEN for outbound calls. Federal Communications Commission (FCC) rules require most providers to implement STIR/SHAKEN on their network IP.
They require providers to certify in the Robocall Mitigation Database that they have implemented STIR/SHAKEN, as part of the TRACED Act, which stands for Telephone Robocall Abuse Criminal Enforcement and Deterrence.
The law defines the risks and penalties for fraudulent telephone communications.
How STIR/SHAKEN and 10DLC Relate
10-digit Long Codes (10DLC) are local long code numbers approved by local mobile number operators for application-to-person (A2P) messaging. Since they’re pre-approved by phone network operators, businesses avoid any penalties due to non-compliance with messaging regulations.
A2P 10DLC focuses on SMS authentication, while STIR/SHAKEN concentrates on caller ID authentication. Together, they improve business communications’ security and integrity.
They complement each other. 10DLC compliance requires businesses to register their brand and campaigns, reducing the possibility of unauthorized communications. STIR/SHAKEN prevents caller ID spoofing, creating a more secure environment for voice communication.
Is STIR/SHAKEN Mandatory?
Yes, it’s mandatory in the U.S. to implement the protocol from June 30, 2021, for large carriers and June 30, 2022, for smaller and rural carriers. The TRACED Act mandates the implementation of STIR/SHAKEN.
U.S. consumers alone received over 60 billion robocalls in 2023. With the upward trend of robocalls and call frauds, regulatory bodies in different countries encourage businesses to adopt robust authentication measures within implementation deadlines.
Recently, the FCC adopted new rules to strengthen its consumer protections, allowing carriers to more aggressively block malicious calls and text messages from noncompliant telephone networks.
Other countries are making some developments in call authentication while preventing caller ID spoofing. An estimated 25% of all incoming calls on Canadian phone numbers were robocalls in 2021. To combat this, the U.S. FCC pledged cooperation with Canada in its enforcement efforts.
Stay Vigilant With Nextiva
After enforcing regulations to mitigate robocalls, there have been some decreases in complaints filed with the Federal Trade Commission. However, they’re still a problem.
Stay ahead of the STIR/SHAKEN requirements with a fully compliant business VoIP platform from Nextiva. It’s easy to set up, and your team will love its functionality. Plus, you’ll also uphold customer trust in your brand so you can scale your company faster.
Business VoIP service done right.
Integrate secure phone service, SMS, video, and team chat in ONE platform.
















 VoIP
VoIP 






![Five9 vs. NICE CXone: A Detailed Comparison [2025 Guide]](https://www.nextiva.com/cdn-cgi/image/width=1200,height=676,fit=cover,gravity=auto,format=auto/blog/wp-content/uploads/sites/10/2024/04/five9-vs-nice-incontact.webp)
