Is VoIP Secure? — That’s a question several IT leaders have been asking lately. And the recent compromise on 3CX’s VoIP via a supply chain attack isn’t helping matters either [*].
For the most part, the nature of VoIP involves transmitting voice communications over the internet rather than through traditional telephone lines.
An advanced way of looking at this is VoIP converts analog voice signals into digital data packets, which are then transmitted over the internet or other packet-switched networks. And the best part about VoIP is its cost effectiveness, flexibility and integration capabilities.
However, the very nature of transmitting voice communications over the internet opens up several vulnerabilities that can be exploited by cybercriminals.

With this in mind, more questions roll in — how do you secure your VoIP calls? Best practices? Mitigation tactics? All of this and more will be answered in this guide.
But first —
How Does VoIP Work?
Here’s a quick run down of how the VoIP system works:
- Voice signal conversion: When you speak into a VoIP-enabled device (like a smartphone, computer, or VoIP phone), it converts your voice into digital data. This conversion is done by your device’s microphone and an analog-to-digital converter (ADC), transforming the sound waves of your voice into digital packets of data.
- Data compression: Next, it compresses your digital voice data using a codec (coder-decoder).
💡Note → This step is important for reducing the size of the data packets so they can be transmitted more efficiently over the Internet. Different codecs offer a balance between voice quality and the amount of data bandwidth used.
- Packetization: The compressed digital data is divided into small packets. Each packet is wrapped with a header that contains information necessary for routing and reassembling the packets in the correct order once they reach their destination.
- Transmission: The packets are sent over the Internet or any other IP network. To reach the destination, they travel through various routers and networks, which is determined by the routing information in each packet’s header. The Internet’s structure allows these packets to take the most efficient path available at the time of transmission.
- Reassembly: Once the data packets arrive at their destination, they are reassembled into the original sequence to accurately reproduce the spoken words. This reassembly takes into account any packets that may have arrived out of order or were lost during transmission.
- Decompression and Conversion: The digital data is then decompressed (if necessary) and converted back into analog sound waves using a digital-to-analog converter (DAC).
💡Note → This step is the reverse of what happened at the sender’s end.
- Playback: Finally, the analog signal is sent to the speaker of the receiving device, allowing the recipient to hear the sender’s voice as if it were a traditional phone call.
💡Recommended → How Does VoIP Work? The Beginner’s Guide To VoIP Phone Systems
Why VoIP security matters
Security is essential to every business. It doesn’t matter if you have a large organization or a small business. A disruption to your phone system would be nothing short of catastrophic.
Voice over Internet Protocol (VoIP) is no different. The lower costs of VoIP entice a business owner. An attacker would love to exploit your VoIP network when you’re not looking.
The good news is that VoIP is quite secure today. It has endured even after two decades of penetration testing. Overall, VoIP service providers are reliable and secure, even as the nature of security threats continues to evolve.

JP Morgan surveyed business leaders and discovered that 94% of companies had taken steps to harden their infrastructure. Malware, payment fraud, and data breaches topped their worries.
Unlike other IT security threats, Voice over IP presents new opportunities for attackers. Top risks include call interception, caller ID spoofing, vishing, and Denial of Service (DoS) attacks. We’ll get more into those specifics later.
VoIP security isn’t only about call encryption. It’s about the level of trust that’s conveyed over a voice and text network. Your business communication platform can carry out more attacks if it’s compromised.
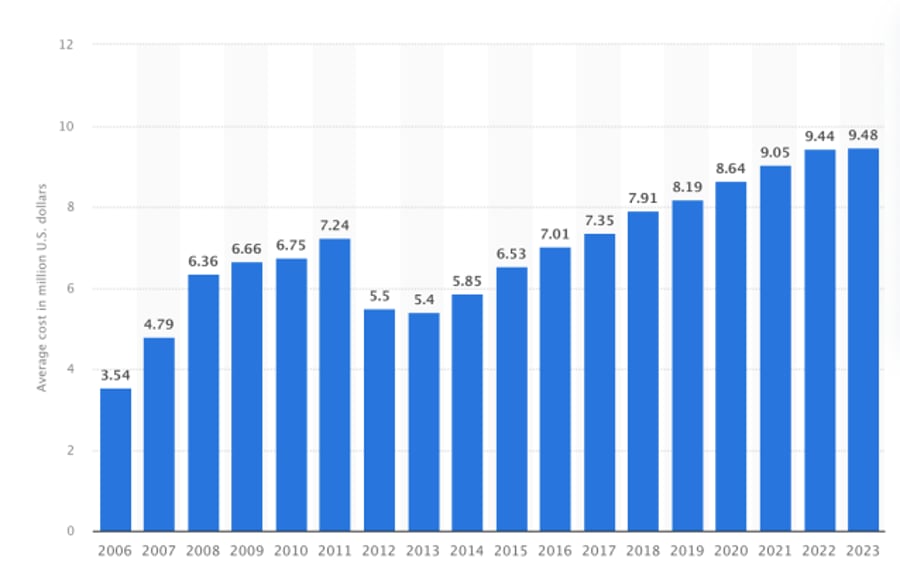
The cost of a breach continues to rise every year. On average, a security breach in the United States costs $9.4 million, according to reports from Statista.
Attackers can carry out attacks with the help of VoIP, such as:
- Social engineering via phone calls.
- Disclosing internal Wi-Fi network passwords.
- Dialing expensive phone numbers (toll fraud).
- Intercepting multi-factor authentication text messages.
- Gaining unauthorized access under the false pretext to data networks.
For example, Twitter faced several coordinated attacks. The company is no stranger to VoIP security risks, and former CEO Jack Dorsey was targeted in a fraudulent number porting request last year.
This security issue likely had little to do with strong passwords. It was worse.
Social engineering can help carry coordinated attacks against known VoIP users. The Network Operations Center (NOC) staff and customer service teams are always top targets. All it takes is granting unauthorized access to your company once, and your intrusion detection system becomes worthless.
Famed hacker security consultant Kevin Mitnick compromised systems not only with technical skills. He exploited his target’s willingness to help. The best defense here is to educate your staff about how to spot social engineering.
The good news is there are effective countermeasures to mitigate VoIP security issues. Professional VoIP networks have become resistant to abuse from known and unknown actors.
Let’s look deeper at the security threats plaguing business phone systems.
Related: How Does VoIP Work? The Beginner’s Guide To VoIP Phone Systems
Traditional Phone Systems vs. VoIP

People placed calls over the Public Switched Telephone Network (PSTN) for over a century. This voice network is analog. It remains vulnerable anywhere physical access to wiring is possible.
This legacy phone system is also known as the Plain Old Telephone System (POTS). Calls are connected using audio signals, which attackers can intercept with ease.
In the diagram below, you can see that calls pass through analog terminals into a Central Office. Phone companies today have established security measures and protocols to ensure security between Central Offices. But that security doesn’t extend to your internal phone system.
An entire subculture formed around the vulnerabilities of business telephone systems. Phreaking, a portmanteau of phone + hacking, is a practice of exploring vulnerable phone systems. In the 1970s, it was possible to get free calling over the PSTN. In the late 90s, phreakers pivoted toward Private Branch Exchange (PBX) equipment. That is, they can springboard attacks from insecure corporate phone systems. Head to your local Barnes & Noble to pick up 2600 and read about the vulnerabilities of an old Lucent or Avaya phone system.
Telephone networks today separate voice traffic from the signaling to establish calls using SS7 protocol. Despite this, many PBX systems remain vulnerable, and attackers will find them.
Voice over Internet Protocol is different.

Calls are established using the SIP protocol. Session Initiation Protocol (SIP) acts as a signaling protocol for reliable internet telephony. A SIP server compresses voice traffic into media streams and sends them over an internet connection.
It’s clear why large companies and small businesses flocked to make calls over the internet. It saves on IT and communication expenses and provides users with a ton of flexibility to work from home.
VoIP phone systems use the same data network to establish phone calls. The VoIP provider exclusively handles all VoIP traffic. IT staff only need to maintain a secure network for their staff.
In the diagram below, a stable network connection is needed for VoIP phone service. You don’t need to build or maintain the VoIP infrastructure.
The biggest difference here is that phones and identities exist virtually. This means users can take their VoIP phones with them and work from anywhere. Additionally, it means people can use SIP calling apps, also known as a softphone, for calling.

VoIP phone services offer many security advantages over traditional phone systems. Top benefits include:
- Real-time monitoring of calling plan usage.
- Strict enforcement of toll-free calls.
- Call encryption to prevent eavesdropping.
- Robust voicemail features with email delivery.
So, what about when VoIP calls reach the PSTN?
Reputable VoIP providers maintain military-grade security. They use Session Border Controllers (SBCs) for optimal security and performance. An SBC acts as a firewall that maintains performance and logical call routing. Operators maintain high standards to patch for security vulnerabilities and manufacturer’s firmware updates.
Call logs for an old-school phone system are often very limited. This makes tracking down stolen business data nearly impossible. More PSTN risks fall under gaps in business continuity.
For instance, many PBX phone systems aren’t well supported, replacement parts are expensive, and finding qualified technicians is challenging. An outage could knock out your business communication for weeks.
The bottom line is that VoIP phone systems offer better privacy, security, and reliability for businesses.
Top VoIP security threats
You’re probably curious about the types of VoIP security issues that are out there. Here’s a rundown of what you’ll need to fend against.
- Denial of Service (DoS) – This attack starves the network of resources to interrupt phone service and drop phone calls. This can degrade call quality, latency, and uptime for a call center.
- War dialing – This type of attack involves controlling your PBX to “scan” other telephone networks. It works by dialing numbers to connect to modems or other interesting extensions.
- Toll fraud – Like war dialing, this requires access to call an outside line from your phone system. Attackers can dial expensive international numbers that rack up expensive toll charges.
- Phishing – This VoIP hack preys on unsuspecting users who trust their caller ID. Victims divulge details about the internal IP network, passwords, or other sensitive data.
- Call interception – Attackers use unsecured networks to intercept unencrypted SIP traffic. To make matters worse, this can include video as well.
- Spam – It should come as no surprise the voicemail box is a common target for robocalls and other phone scams. Many use restricted or “Private” caller ID.
- Malware – Attackers use different malicious software to phone or email credentials. This can open up more opportunities to infiltrate your network and exfiltrate sensitive business data.
These threats are most alarming if you’ve set up a DIY phone system. As the company has expanded, it’s no longer the right fit. For instance, a self-hosted Asterisk PBX might suffice for some, but it’s an attractive target for hackers. VoIP attacks might be silent and undetected for months.
So, what should you look for in a VoIP service provider? It’s tempting to look only at phone system costs, but there’s more to consider when it comes to security.
Related: Healthcare Call Center Best Practices for Better Patient Care
Choosing a secure VoIP provider
The security of your phone system comes down to implementation and compliance with security protocols.
As with any cloud PBX, make sure the provider meets security requirements. These vary depending on your industry and specific needs. The best way to begin this investigation is by asking your provider:
- What accreditations do you have?
- Do you use third-party tools or software?
- How do you train and retrain staff?
- How do you respond to security incidents?
- Do you offer TLS and SRTP call encryption?
Accreditations
Once you’ve answered these questions, dive deeper into your own VoIP requirements. Listed below are the top certifications to keep in mind:
- HIPAA Compliance – Health Insurance Portability and Accountability Act (HIPAA) mandates that healthcare service providers secure patient data. These rules also apply to their phone systems, such as voicemail and call recordings. VoIP servers need to be configured to protect patient privacy.
- ISO/IEC 20071 – This global standard establishes that organizations assess and respond to security threats. It means that the organization has implemented rigorous information security controls.
- PCI Compliance – Payment Card Industry (PCI) compliance mandates that you must secure your infrastructure if you accept credit cards. It mandates operating system updates and secured VLANs. It also requires penetration testing against your organization’s IP addresses. Securing payment data is table stakes for e-commerce. You risk higher transaction fees and penalties if your VoIP solution isn’t PCI-compliant.
- SOC 2 Compliance – Service Organization Control (SOC) compliance consists of practices to ensure consumer trust. Unlike other standards, there’s flexibility across five areas: privacy, security, availability, and data integrity. Many reputable SaaS companies and cloud-based services meet SOC 2 compliance.
It’s easy to see how these certifications can give you greater peace of mind. It can be challenging to certify your on-premises PBX or home-grown phone system running on Amazon or Google Cloud. You don’t want to take chances when it comes to VoIP security.
Ask your VoIP provider for certifications and compare them to your needs. If you’d like a summarized version of all the above information, check out our quick three-minute video on VoIP security below:

Related: A 5-Step VoIP Implementation Guide (+How to Do it Yourself)
Customer communications
Another factor to consider is how well the company communicates with customers. How can you tell? Look for its status page, which is also known as a trust page. The example shown below is the Nextiva Status page.

Status pages detail updates about the VoIP system and incidents affecting voice service. Are they specific? Are they helpful? Are updates timestamped?
Confirm if there has been any widespread downtime or outages. Look for 99.999% uptime, meaning there are only six minutes of downtime annually. Additionally, look for planned maintenance to apply updates to the VoIP network. These often include essential operating system updates.
The reality of IP telephony is that some interruptions might occur, but it matters how your VoIP vendor communicates with you about it.
Call encryption
Besides certifications and straightforward customer communication, you want call encryption in 2020. Call encryption uses Transport Layer Security (TLS) and Secure Real-time Transport Protocol (SRTP). These VoIP protocols work together to establish high-grade security in every call.
Unencrypted networks are prone to snooping. By contrast, data that is encrypted is of no use to anyone who manages to record the data transmission. Encryption that runs from the phone to the service provider is important. Data should be encrypted on every possible layer.
For the greatest interoperability, SIP isn’t encrypted. Since IP telephony uses the IP stack, encryption is managed by the transport layer. When enabled, the VoIP call session and the accompanying call data isn’t available to data thieves.
Ask your VoIP provider about call encryption to ensure your SIP devices can use TLS and SRTP.
VoIP security for healthcare providers
If your company manages patient data or otherwise needs to follow HIPAA, keep reading.
Medical offices must protect patient privacy by configuring their communications systems. This includes your VoIP phone service. Healthcare providers are top targets because patient information is frequently used to carry out identity theft.
Voice over IP networks meets HIPAA requirements when they put in place proper security measures. Ensure your VoIP provider has agreements with business associates to maintain compliance.
VoIP considerations to meet HIPAA

Some VoIP users are unaware that they are required to disable certain services to stay compliant. Voicemail transcription, voicemail-to-email attachments, and visual voicemail aren’t allowed.
With Nextiva, you can be sure that your VoIP solution is HIPAA-compliant. Let us know, and we can provision your account on our secure VoIP servers.
VoIP security best practices
Security isn’t as obscure as some might think. We’ve simplified the best practices to ensure optimal security for your organization.
Here is how you can protect your VoIP network from threats.
- Enforce a strong password policy. Strong passwords are essential to securing your phone system. Use a combination of letters, numbers, and non-alphanumerics. Ensure that employees don’t store passwords in text files or Post-It notes on their computers.
- Apply operating system updates often. Applying operating system updates is a given for most systems administrators. Encourage your users to accept OS updates for their iPhone or Android. These updates can guard against malicious software and exploits.
- Set up a Virtual Private Network (VPN) for remote staff. VPNs can encrypt all traffic regardless of where the employee works. It’s ideal for work from home staff. Consider a business-grade VPN from Cisco, Sophos, or Cloudflare. Recent academic research has shown VPNs don’t degrade call quality.
- Require Wi-Fi encryption. Activate WPA2 on your company’s wireless networks. Instruct employees also use this encryption for their Wi-Fi network. As a best practice, update your Wi-Fi password every year.
- Review your call logs. Examine your company’s call logs to identify any unusual calling trends or behavior. Set up a helpful dashboard using a call analytics feature to monitor call volume on a weekly and monthly basis.
- Restrict your calling and block private calls. Unless your company does business overseas, you don’t need to dial international numbers. Better yet, only grant access to international calling to those who call abroad. Confirm your VoIP service blocks 1-900 numbers to prevent toll fraud. Enable call blocking to screen restricted/private calls with a message instructing them to enable their caller ID.
- Deactivate inactive accounts. When employees leave the company, don’t forget to notify your IT staff. By disabling employee accounts promptly, you can minimize workplace disruptions. From a technical standpoint, you don’t want VoIP accounts to remain functional without a real user assigned to it.
- Encourage your staff to report strange behavior. Ask your team to report missing voicemails and ghost calls. A ghost call is when your phone rings without a caller. Additionally, recommend they don’t store voicemail messages longer than needed.
- Implement remote device management. On an enterprise level, having the ability to wipe a device remotely is essential. Issue laptops with remote management so you can track and wipe a device in the event of theft or compromise.
- Educate users on security practices. Remind users that you won’t ever need their password. Train them to spot phishing and social engineering scams. Conduct regular security assessments to discover emerging vulnerabilities. Last but not least, make sure they know who to contact in the event of a security breach.
While a lot of these best practices overlap with network security, look at them through the lens of an attacker.
Executives depend on you to keep them safe from the ever-changing security landscape. By following these, you will minimize the impact of a security incident.
The future of securing phone systems
VoIP has matured from a personal service to an essential business communications platform.
The grass is always greener where you water it. VoIP has been put through its paces to prove valuable for organizations. Secure SIP-based calling is now the standard.
Maintaining an on-premises PBX and other telephony equipment is a big responsibility. The phone system is no different as organizations offload their email systems and web hosting to the cloud.
A cloud phone system like Nextiva allows IT staff to tackle bigger projects. Instead of tinkering with old equipment, they can equip the company with a remote workforce.
Final thoughts on VoIP security

Organizations that secure voice traffic are more resilient than those that sit idle. If there’s anything 2020 taught us, it’s that you must be prepared for every contingency.
According to findings from the 2020 U.S. CEO survey from PwC, 53% of CEOs were “extremely concerned” about cybersecurity. This is astounding, given that cyber threats outweighed policy, trade, government regulation, and geopolitical uncertainty.
Much of the security responsibility rests with maintaining operational security. You can better mitigate threats by accepting VoIP phones as powerful network appliances.
Despite all this, secure VoIP providers can only do so much. You must fortify your internal network defenses and educate users first.
A reputable business phone service can be the assurance you need to maintain a secure calling environment. Check their certifications and research their reliability, security measures, and call encryption capabilities.
The Phone System IT Loves
Enterprise security. Uncompromising features. See Why IT Teams Trust Nextiva for Their Company’s Phone Service.
















 VoIP
VoIP